Security | Data Privacy
In today's digital era, safeguarding your data is more than a necessity—it's a top priority. We acknowledge the critical importance of this issue and position ourselves as leaders in data privacy and security.
How does it work?
Our comprehensive suite of security features is meticulously engineered to safeguard your data against the ever-evolving landscape of cyber threats, ensuring that your information remains secure, private, and under your control.
End-to-End Encryption
Advanced Threat Detection
Secure User Authentication
Data Anonymization
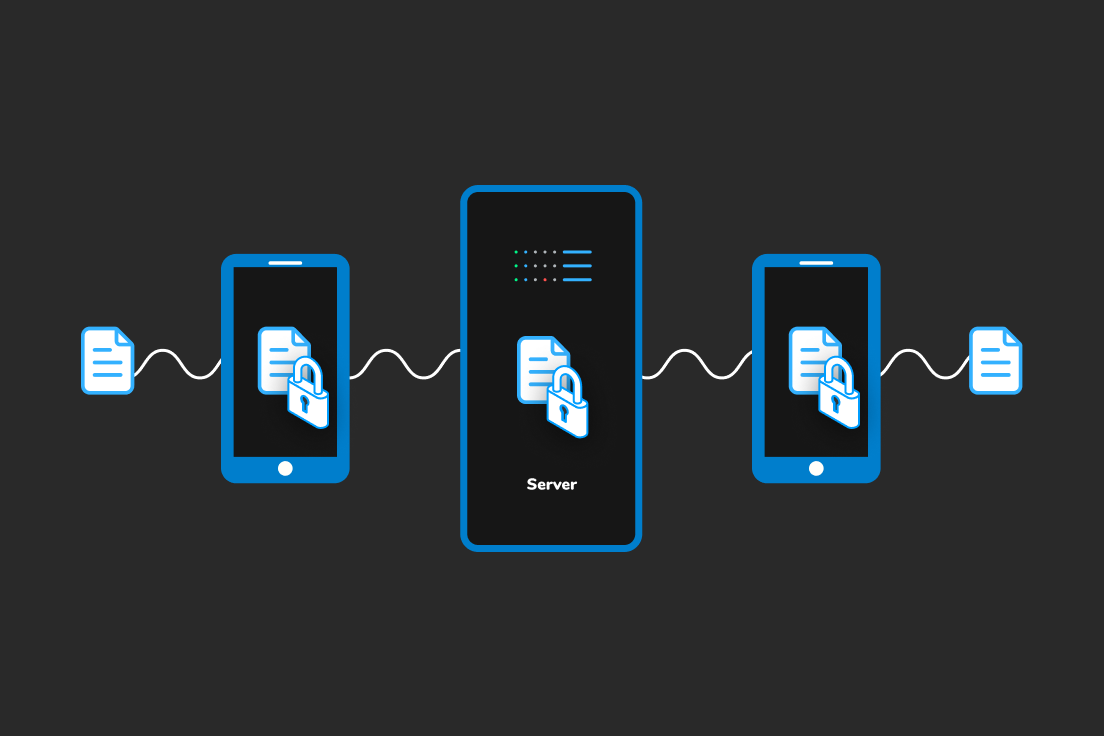
End-to-End Encryption
At SWRM, we implement end-to-end encryption to secure data at every point of its journey. This means your data is encrypted from the moment it leaves your device until it reaches its destination, making it unreadable to anyone but the intended recipient.
- Military-grade encryption standards to protect data in transit and at rest.
- Automatic encryption for all collected data, ensuring privacy and security.
Advanced Threat Detection
Leveraging cutting-edge AI and machine learning technologies, our platform provides real-time threat detection and response. This proactive approach allows us to identify and neutralize threats before they can impact your data.
- Continuous monitoring and analysis of data traffic for unusual patterns.
- Instantaneous automated response to identified threats, minimizing potential damage.

Secure User Authentication
SWRM employs a multi-factor authentication system that verifies each user's identity through multiple checkpoints. This layered security ensures that only authorized personnel can access sensitive data, adding an extra layer of protection.
- Options for biometric verification, OTPs, and security tokens.
- Customizable authentication processes tailored to your organization's needs.
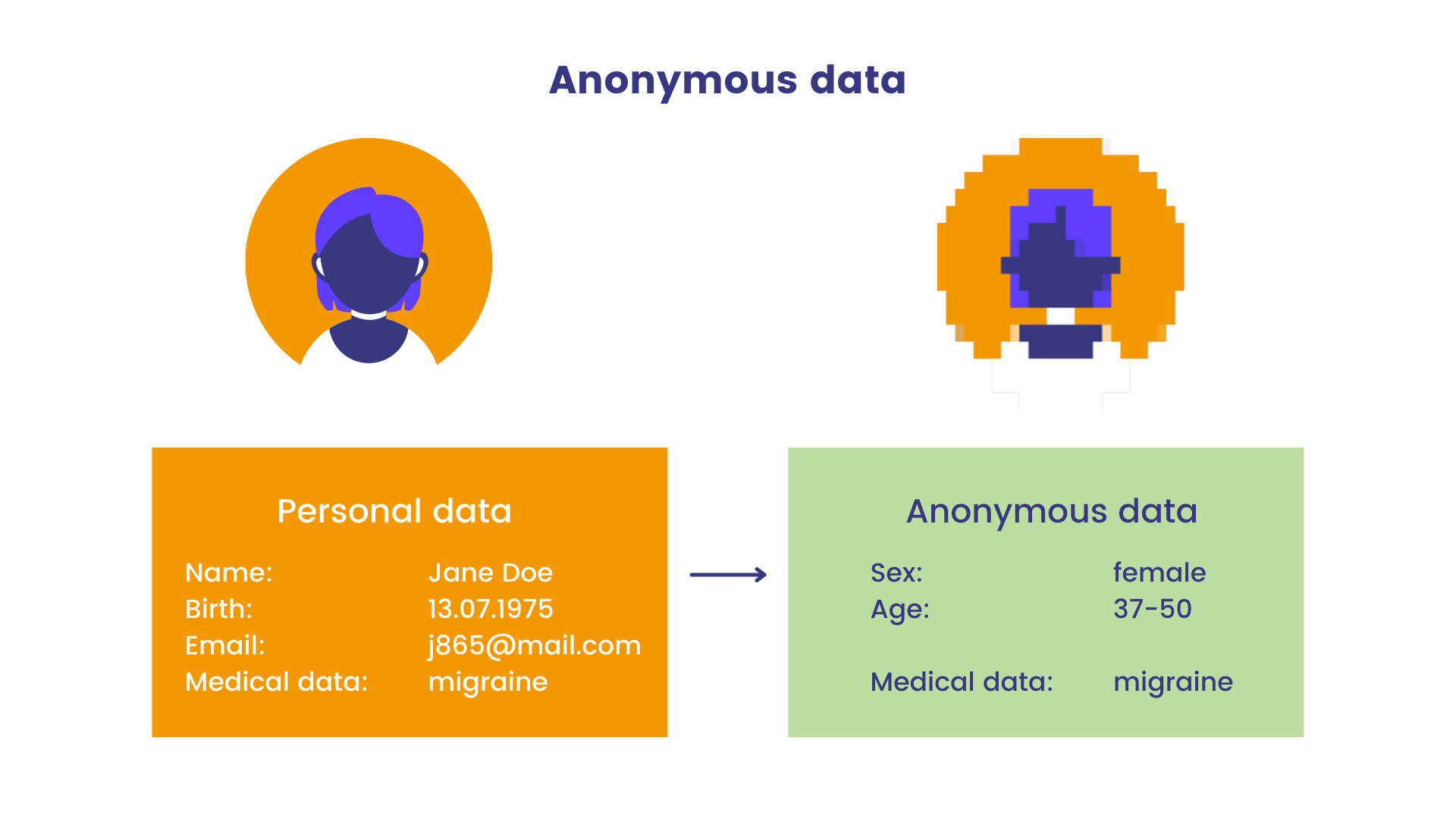
Data Anonymization
Understanding the paramount importance of privacy, SWRM incorporates data anonymization techniques. By removing personally identifiable information from the datasets, we ensure that the data remains confidential and the privacy of individuals is maintained.
- Automated anonymization of sensitive data to uphold privacy standards.
- Compliance with global data protection regulations, ensuring ethical data handling.




